C Program To Implement Dictionary Using Hashing It Out
Stephen Diehl (@smdiehl) This is the fourth draft of this document. This code and text are dedicated to the public. General hash function algorithm implementations for string hashing in the object pascal, c and c++ programming languages. In computing, a hash table (hash map) is a data structure which implements an associative array abstract data type, a structure that can map keys to values. Later in this chapter, we will find out the result from the execution of the example above. The Abstract Data Structure “Dictionary” (Associative Array, Map).
Generate Secure Password Hash : MD5, SHA, PBKDF2, BCrypt Examples. A password hash is an encrypted sequence of characters obtained after applying certain algorithms and manipulations on user provided password, which are generally very weak and easy to guess. There are many such hashing algorithms in java also, which can prove really effective for password security.
In this post, I will discuss some of them. Note: Please remember that once this password hash is generated and stored in database, you can not convert it back to original password. Each time user login into application, you have to regenerate password hash again, and match with hash stored in database.
So, if user forgot his/her password, you will have to send him a temporary password and ask him to change it with his new password. It’s common now- a- days, right? Sections in this post: Simple password security using MD5 algorithm.
Making MD5 more secure using salt. Medium password security using SHA algorithms. Advanced password security using PBKDF2. With. Hmac. SHA1 algorithm. More Secure password hash using BCrypt and SCrypt algorithms. Final notes. Simple password security using MD5 algorithm. The MD5 Message- Digest Algorithm is a widely used cryptographic hash function that produces a 1.
- Output: To know more go to the following link: Difference Between Const, ReadOnly and Static ReadOnly in C#; Constant VS ReadOnly In C#; 10. What is the difference.
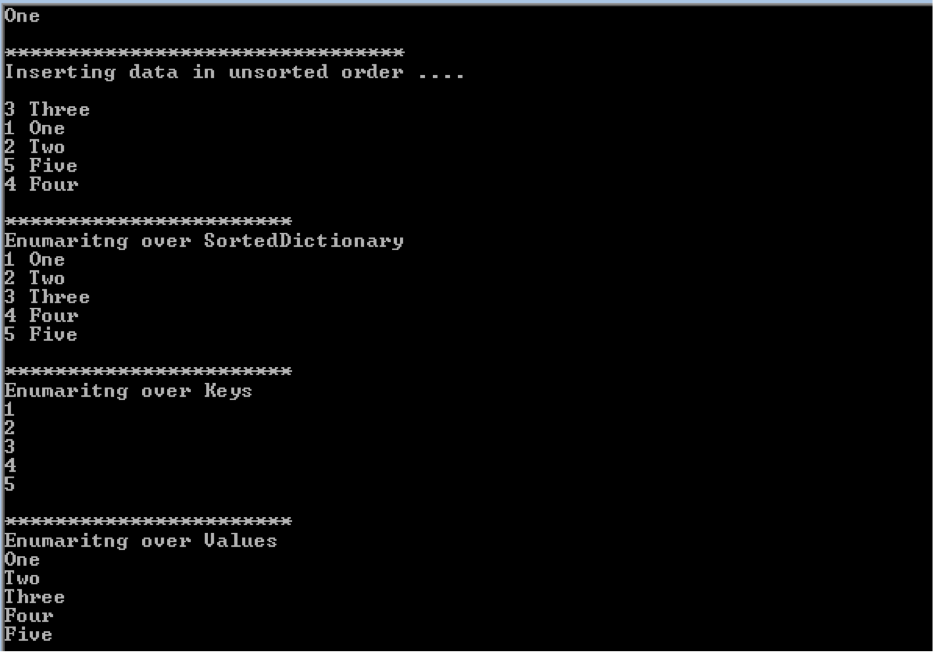
- Hash Tables By Eric Suh Hash tables are an efficient implementation of a keyed array data structure, a structure sometimes known as an associative array or map.
- IronPython aims to be a fully compatible implementation of the Python language. At the same time, the value of a separate implementation than CPython is to make.
- How to Write a Spelling Corrector One week in 2007, two friends (Dean and Bill) independently told me they were amazed at Google's spelling correction.
It’s very simple and straight forward; the basic idea is to map data sets of variable length to data sets of a fixed length. In order to do this, the input message is split into chunks of 5. A padding is added to the end so that it’s length can be divided by 5. Now these blocks are processed by the MD5 algorithm, which operates in a 1. After applying MD5, generated hash is typically a 3.
Here, the password to be encoded is often called the “message” and the generated hash value is called the message digest or simply “digest”. It’s main advantages are that it is fast, and easy to implement. But it also means that it is susceptible tobrute- force and dictionary attacks.
Rainbow tables with words and hashes generated allows searching very quickly for a known hash and getting the original word. Also, It is not collision resistant: this means that different passwords can eventually result in the same hash. Double Clutch Liz Reinhardt Pdf Free here. Still, if you are using MD5 hash then consider adding some salt to your security. Making MD5 more secure using salt. Keep in mind, adding salt is not MD5 specific.
You can add it to other algorithms also. So, please focus on how it is applied rather than its relation with MD5.
Wikipedia defines salt as random data that are used as an additional input to a one- way function that hashes a password or pass- phrase. In more simple words, salt is some randomly generated text, which is appended to password before obtaining hash. The original intent of salting was primarily to defeat pre- computed rainbow table attacks that could otherwise be used to greatly improve the efficiency of cracking the hashed password database. A greater benefit now is to slow down parallel operations that compare the hash of a password guess against many password hashes at once. Important: We always need to use a Secure.
Random to create good Salts, and in Java, the Secure. Random class supports the “SHA1. PRNG” pseudo random number generator algorithm, and we can take advantage of it. Let’s see how this salt should be generated.
Note that if a seed is not provided, it will generate a seed from a true random number generator (TRNG). Now, lets look at the modified MD5 hashing example. Salted. MD5. Example.
Because when user login back in system, you must use only originally generated salt to again create the hash to match with stored hash. If a different salt is used (we are generating random salt), then generated hash will be different. Also, you might heard of term crazy hashing and salting. Yamaha Popcom Software Download. It generally refer to creating custom combinations like: salt+password+salt => hash. Do not practice these things. They do not help in making hashes further secure anyhow.
If you want more security, choose a better algorithm. Medium password security using SHA algorithms.
The SHA (Secure Hash Algorithm) is a family of cryptographic hash functions. It is very similar to MD5 except it generates more strong hashes. However these hashes are not always unique, and it means that for two different inputs we could have equal hashes. When this happens it’s called a “collision”. Singer Manual 3232 En Youtube. Chances of collision in SHA is less than MD5. But, do not worry about these collisions because they are really very rare.
Java has 4 implementations of SHA algorithm. Bezier Curves Sketchup Plugin Folder here. They generate following length hashes in comparison to MD5 (1.
SHA- 1 (Simplest one – 1. Hash)SHA- 2. 56 (Stronger than SHA- 1 – 2. Hash)SHA- 3. 84 (Stronger than SHA- 2. Hash)SHA- 5. 12 (Stronger than SHA- 3. Hash)A longer hash is more difficult to break. That’s core idea.
To get any implementation of algorithm, pass it as parameter to Message. Digest. But the problem today is that hardwares have become so much fast that any brute force attack using dictionary and rainbow tables, any password can be cracked in some less or more time. To solve this problem, general idea is to make this brute force attack slower so that damage can be minimized. Our next algorithm, works on this very concept. The goal is to make the hash function slow enough to impede attacks, but still fast enough to not cause a noticeable delay for the user. This feature is essentially implemented using some CPU intensive algorithms such as PBKDF2, Bcrypt or Scrypt. These algorithms take a work factor (also known as security factor) or iteration count as an argument.
This value determines how slow the hash function will be. When computers become faster next year we can increase the work factor to balance it out.
Java has implementation of “PBKDF2” algorithm as “PBKDF2. With. Hmac. SHA1“. Let’s look at the example how to use it. If found any difficult then download the sourcecode attached at end of tutorial. More Secure password hash using bcrypt and scrypt algorithms.
The concepts behind bcrypt is similar to previous concept as in PBKDF2. It just happened to be that java does not have any inbuilt support for bcrypt algorithm to make the attack slower but still you can find one such implementation in source code download. Let’s look at the sample usage code(BCrypt. Bcrypt. Hashing. Example. Lets see how to use the implementation. Scrypt. Password. Hashing. Demo. . Adding salt make it further stronger.
MD5 generates 1. 28 bit hash. To make ti more secure, use SHA algorithm which generate hashes from 1. Even SHA hashed secure passwords are able to be cracked with today’s fast hardwares.
To beat that, you will need algorithms which can make the brute force attacks slower and minimize the impact. Such algorithms are PBKDF2, BCrypt and SCrypt.
Please take a well considered thought before applying appropriate security algorithm. To download the sourcecode of above algorithm examples, please follow the below link. Happy Learning !! References: https: //en. MD5https: //en. wikipedia.
PHP: sha. 1 - Manual. Small update.., well more like fix to the obscure function, replace< ? Length != NULL). In most solutions with hash and salt, you were bound to have one extra row in your database that would state, preferably random, salt for that hashed data. If attacker would manage to get drop of your database he would get hashed data and salt that is used with plain data to make it obscure, and then cracking that hashed data would be same as if you didn't add any salt to it. Castlevania Judgment Iso Ntsc And Pal read more. I stumbled upon some functions that would hash data, then input salt into random places in hash and store it in database, but they would still have to write down random parameter used to scramble salt so they could reuse it when validating data.
Getting simple database drop wouldn't help much here, but if they would manage to get their hands on obscuring function too, they could easily see what is salt and what hash. Solutions: 1. Why use extra row to store salt when you can input it in hash. I'm not sure how attackers determine what type of hash are they facing, but I guess it has connection to hash length. In that case, why make attackers job easier and store in database data. Sbloccare Alice Gate 2 Plus Voip Wifi App here. If it's set to 1, strlen of hashed data plus salt would be equal to strlen of hashed data leading attacker to believe there is no salt. Handbook Of Porous Media Pdf Merge on this page.
If you leave $keep. Service Technician Workbench Keygen. Length on NULL, strlen of final result would be strlen(used. If you think about it, constant, but variable value when making input would be same data that is being input. In case we're trying to hash password, and have user A with password . Replace first 5 characters of hashed.
Attacker might not know that hash is salted, and you don't have that extra row in your database stating THIS IS SALT FOR THIS HASH. If he does find out that it is, he wouldn't know what is hashed password and what is salt. If he manages to get access to obscure function, only thing that might help him is value of $h. SLength, where if $h. SLength is set to 1. For example first variation would be hashed.
Even in case he has enough power to crack all 1.